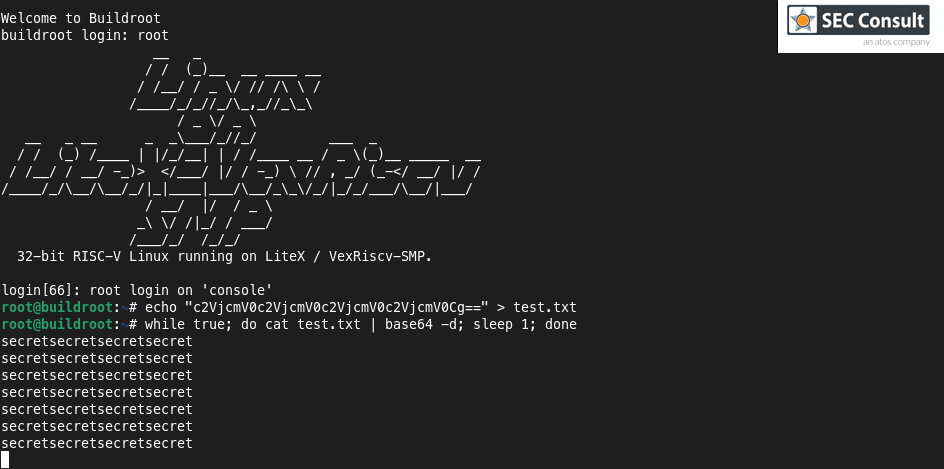
Applied Sciences | Free Full-Text | Cold Boot Attacks on the Supersingular Isogeny Key Encapsulation (SIKE) Mechanism

PPT – Lest We Remember: Cold Boot Attacks on Encryption Keys J. Alex Halderman, Seth D. Schoen, Nadia Heninger, William Clarkson, William Paul, Joseph A. Calandrino, Ariel J. Feldman, Jacob Appelbaum, and